SharkCage: VM secure processor
Recent popularization of virtual machines (VMs) on cloud services has promoted cases that enterprises run their services on external cloud service platforms. In exchange for the huge merits in various aspects such as deployment costs and scaling ease, there is a risk that cloud administrators may abuse their privileges to steal secrets from the customer’s VMs.
This predominance of virtual machine monitors against VMs is similar to that of OSs over applications. Secrets such as licensing mechanisms applications have is held in the registers in CPUs or the main memories in the form of unencrypted data, which is readily browsed and manipulated by malicious OSs or administrators. Illegal copying of software and digital contents is one of the major problems.
Some approaches which enable mandatory access control, namely, limiting administrator’s privileges, have been proposed as solution for those problems. Nevertheless, the approaches which protect applications with processors or virtual machine monitors from untrusted OSs have a major obstacle to their implementation that they have to modify OSs or to support individual OSs to detach wide and deep adhesions between OSs and applications. On the other hand, those which protect VMs with processors from malicious administrators consider only cloud environment, which can be a problem to their popularization cost.
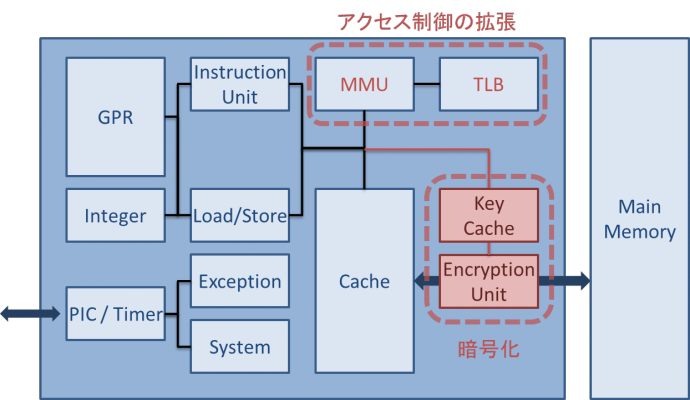
We proposed SharkCage, a new platform to allow the data owners to easily control those privileged accesses against software/hardware attacks caused by malicious administrators. SharkCage can transparently protect VMs without depending on guest OS nor modifying host OS.
This year we have shown integrity verification protocol on multi-processor environment, DMA protocol with secure device, and fast external verification on boot.